Antivirus and Data Classification provider enables customers to ingest events into AWS CloudTrail for security and compliance purposes
January 31, 2023 – Today, data security software provider Cloud Storage Security (CSS) is among the first Amazon Web Services (AWS) Partners to integrate with AWS CloudTrail Lake to consolidate activity data reporting. This is noteworthy as historically AWS CloudTrail did not ingest third party data; it logged data generated from AWS services. With this integration, customers can now ingest and analyze events in a CloudTrail-compatible schema from the CSS console to streamline auditing, security investigation, and operational troubleshooting.
Solution Overview
CSS is an AWS Public Sector Partner and AWS Marketplace seller. CSS has an AWS qualified software offering, AWS security competency, and an AWS Authority To Operate designation. The company helps customers prevent the spread of malware, locate sensitive data, and perform storage assessments for AWS services such as Amazon Simple Storage Services (Amazon S3).
|
AWS and CSS teamed to deliver this integration for AWS CloudTrail Lake that allows you to simplify and streamline the process of consolidating activity data from AWS and CSS to enhance visibility across environments and applications. |
AWS CloudTrail is a global managed service that can record events from over 150 AWS services (and now AWS Partners) with support for all regions. AWS CloudTrail Lake, is a managed security and audit data lake within CloudTrail that lets customers query and analyze events recorded by AWS CloudTrail.
CloudTrail logs, continuously monitors, and retains account activity related to actions across your AWS infrastructure, giving you control over storage, analysis, and remediation actions. Events are delivered to CloudTrail within minutes and most queries complete within seconds. Each API request is recorded as an "event" in a log file that’s stored in Amazon S3 and includes metadata such as the:
-
Timestamp when the call occurred
-
Source IP address
-
Identity of the caller (user, machine or AWS service)
AWS CloudTrail Lake simplifies activity log analysis integrating collection, storage, optimization, and query across multiple sources, AWS Regions, and accounts in a single location. By consolidating these features into one environment, CloudTrail Lake eliminates the need for separate data processing pipelines that span across teams and products. Plus, with immutable event data storage and a default retention period of seven years, CloudTrail Lake can help customers meet the compliance requirements of most use cases.
Get Answers to "Who Did What, Where, and When?"
When you bring CSS logs into CloudTrail, you receive information on the actions a user takes within the CSS console GUI or API, including changes to:
-
CSS console settings
-
Agent settings
-
API deployment
-
Bucket protection (e.g., turned on or off, public access enabled, bucket encrypted)
-
Scan settings (e.g., when a scan was run, initiated, canceled or finished)
-
Permissions/user activity (e.g., who logged in, who initiated a scan, who modified a file)
-
Files (e.g., when a file is modified)
The benefit of this, is that in addition to reviewing the history of all API requests in one centralized location, you can run complex Standard Query Language (SQL) queries across all regions at once to find something that affected multiple applications, not just AWS services.
|
This integration captures and stores audit-worthy event activity and allows you to query all regions at once, meaning you can find something that affected multiple applications, not just Amazon services.
|
Cross referencing logs from the different applications that are fed to CloudTrail not only simplifies audits but also assists with incident response and remediation by providing insight into the who, what, where and when of the event. Common questions you can find answers to include:
-
What is the event or activity that occurred?
-
Was there any unusual activity?
-
What actions were taken?
-
Was it during a maintenance window?
-
Who is the user?
-
When did they access?
-
From where did they log in?
-
What actions did AWS take?
For example, if a customer is using Antivirus for Amazon S3 by CSS and a virus unexpectedly infects their system, they could identify the source of the malicious activity if the CSS console was involved. That is, they could query CSS audit logs within CloudTrail Lake to see whether someone logged into the CSS console, turned off malware scanning, uploaded a file, then turned scanning back on.
To obtain reporting on the security events that the CSS antivirus and classification scan results generate (e.g, how many files were scanned, if an infected file or sensitive data was found, etc.) refer to the CSS console itself.
What It Costs
CSS does not charge customers to bring CSS activity logs into AWS CloudTrail or to query those logs using CloudTrail Lake. AWS CloudTrail charges apply. Please refer to AWS CloudTrail pricing.
How to Enable the CSS-CloudTrail Integration
AWS launched a PutAuditEvents API for CloudTrail Lake and with this new development CSS has created a simple integration so you can capture information and events on user activity from the CSS console.
In a few steps, you can consolidate CSS activity logs together with AWS activity logs in CloudTrail Lake without having to build or manage the event data pipeline.
After you subscribe, deploy and configure the CSS console, simply go to Configuration in the main menu, select Console Settings, and in the CloudTrail Lake Integration section, enable the integration and follow the prompts to connect CSS and CloudTrail Lake. By enabling the integration in CSS, everything is done for you, including creation of the event data store.
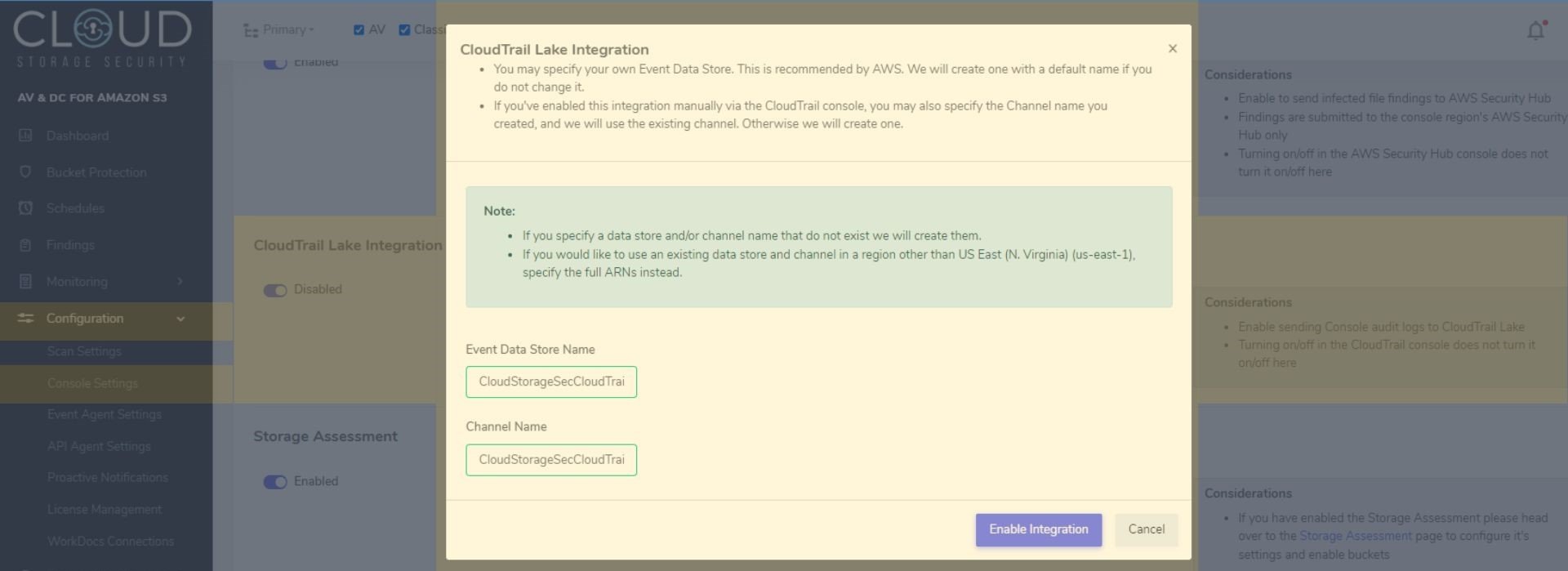
Alternatively, you can discover and enable the CSS integration by navigating to the CloudTrail console where you have a CloudTrail Lake event data store enabled. From there, you will be guided on how to stream events from the CSS console so you can analyze and respond to a consolidated view of activity relating to security, audit, or operational incidents. You can find step-by-step instructions on the AWS News Blog.
CSS solutions can be procured in AWS Marketplace.
About Cloud Storage Security
Agencies and enterprises of all sizes turn to Cloud Storage Security (CSS) to extend data privacy, meet compliance requirements, and manage data security. Specifically, they turn to CSS to prevent the spread of malware, locate sensitive data and assess their storage environment. CSS solutions are used worldwide for applications and data lakes built on cloud storage because they fit into any workflow and data never leaves the customer’s account. Take advantage of a 30 day free trial or contact CSS for more information.
%20(26).png?width=2000&height=1125&name=CSS%20-%20Blog%20(Featured%20Images)%20(26).png)