BLOG
Real-World Success Stories
Learn how CISOs, Engineers, and Security Specialists are solving time-sensitive security challenges, reducing effort, saving money, and achieving compliance.
In recent months, the release of applications such as OpenAI’s ChatGPT have caused a global spike in the popularity of generative artificial...

Aug 18, 2023
In recent months, the release of applications such as OpenAI’s ChatGPT have caused a global spike in the popularity of generative artificial...

Jun 13, 2023
AWS-managed storage services such as Amazon Simple Storage Service (Amazon S3) and Amazon Elastic Block Store (Amazon EBS) are often the data store...
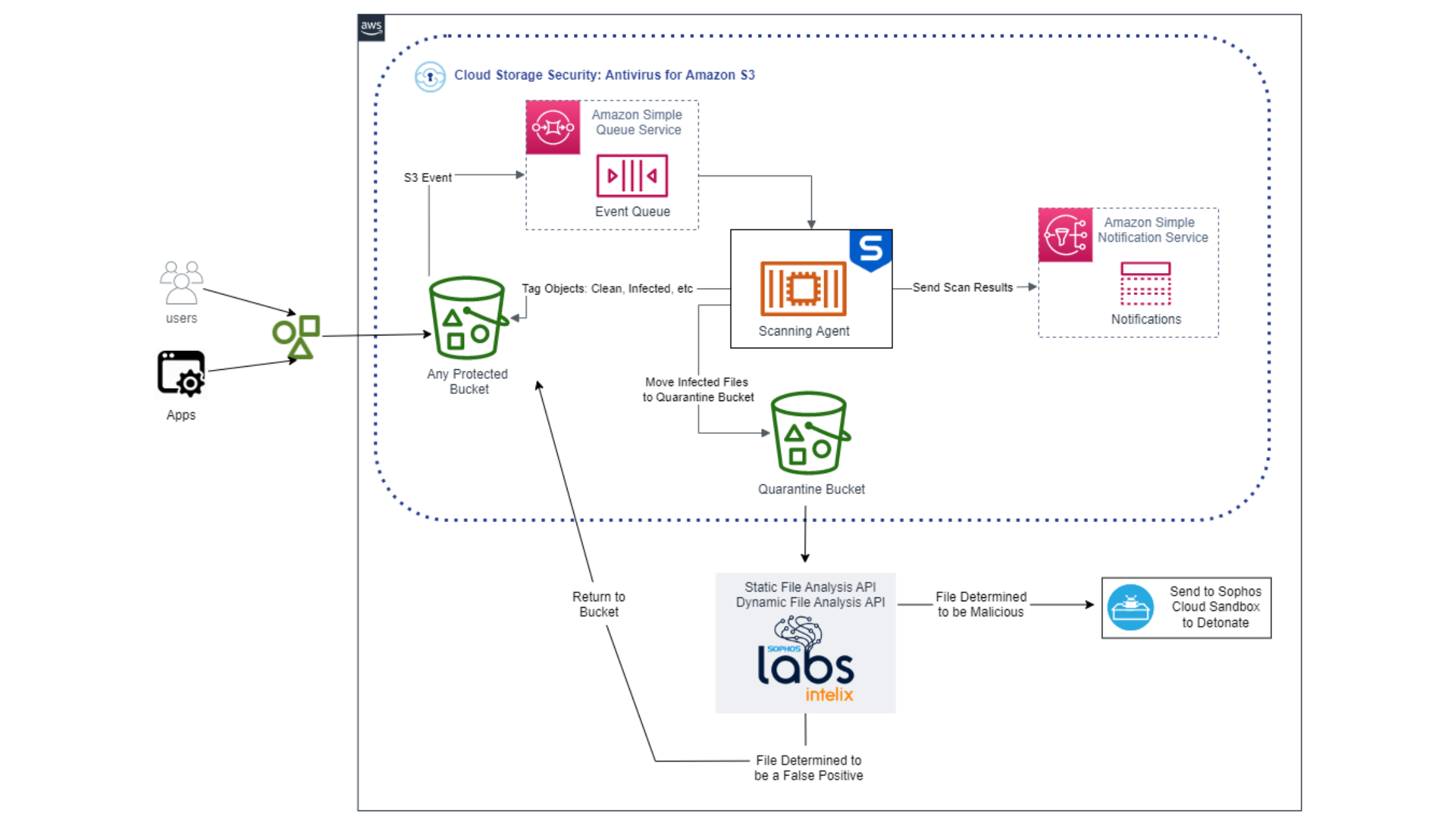
Jul 19, 2022
Amazon Simple Storage Service (Amazon S3) is widely used to run cloud-native applications, build data lakes, archive data, and backup critical data....

Jun 10, 2022
Amazon Simple Storage Service (Amazon S3) launched over 16 years ago and today houses over 200 trillion objects making it one of the most successful...

May 11, 2022
If you ingest files into Amazon S3 from third-party sources that can eventually enter an environment where they become executable, you're opening the...

Mar 31, 2022
AWS celebrated 16 years since the launch of Amazon S3 with AWS Pi Day on March 14, 2022. Since the beginning of the year, some incredible...

Mar 7, 2022
It is well known that malware can disrupt the availability of critical assets and data, impairing an organization’s ability to operate. It is key...

Feb 11, 2022
Customer Challenge
As a fast-growing learning management solution, MindEdge was receiving a growing number of questions from existing and potential...

Feb 11, 2022
Customer Challenge
ADEC Innovations hosts an application on AWS that collects environmental data, charts, and assets from public sources and...
%20(26).png?width=2000&height=1125&name=CSS%20-%20Blog%20(Featured%20Images)%20(26).png)




