
On January 5, 2023, AWS automated server-side encryption for all new objects in Amazon Simple Storage Service (SSE-S3). In this article, we review SSE-S3 (some features may surprise you), discuss how to assess encryption status (with and without help), and touch on how to encrypt existing objects in S3.
A Look at SSE-S3
With server-side encryption, data at rest is protected; data is encrypted before it is saved and then decrypted when it is downloaded. With this update, Amazon S3 automatically applies SSE-S3 to all new buckets and existing buckets that lack a customer configured/default encryption setting. Every object put into Amazon S3 going forward is encrypted with SSE-S3 by default while objects created prior to January 5 do not have SSE-S3 applied by default. There is no additional cost for default encryption with SSE-S3, although requests to configure the default encryption feature incur standard Amazon S3 request charges.
|
With SSE-S3, Amazon S3 automatically encrypts newly created objects. This means objects that exist prior to the launch of SSE-S3 in January 2023 aren’t automatically encrypted. |
SSE-S3 uses 256-bit Advanced Encryption Standard (AES-256). With SSE-S3, when an object is PUT into S3, AWS generates a unique key to encrypt the data and then encrypts that key with a root key that’s regularly rotated. When you GET an object, Amazon S3 automatically fetches and decrypts the key to decrypt the object before it’s sent back to you. You don’t have to take any additional steps to establish a base level of default encryption (unless you proactively choose to change the configuration by enabling one of the other two encryption options offered by AWS: server-side encryption with AWS Key Management Service (SSE-KMS) or server-side encryption with customer-provided keys (SSE-C)). With the rollout of SSE-S3, encryption for new object uploads can no longer be disabled.
SSE-S3 is a fantastic step forward for enhancing data security, but it only applies to new objects. Security best practices dictate that you should verify encryption settings on all objects. Moreover, encryption status should be revisited periodically to avoid configuration drift. These factors warrant an assessment that provides overall encryption status of both new and existing objects.
How to Tell if Encryption is Enabled on Your Buckets
Currently, AWS reports on SSE-S3 in AWS CloudTrail data event logs; the AWS article Amazon S3 Encrypts New Objects By Default includes steps on how to verify encryption using CloudTrail. In the future, AWS will provide encryption status in other Amazon S3 tools such as Amazon S3 Inventory and Amazon S3 Storage Lens.
To help manage and simplify the verification process, Cloud Storage Security (CSS) also reports on encryption status AND we provide insight for both new and existing objects. Our solutions include malware scanning, sensitive data discovery and storage assessments for AWS-managed storage services. Every CSS report is designed to include all buckets across all regions in the account in which the CSS console is running as well as any active linked accounts. We report on encryption status no matter the type of encryption applied. You decide which accounts to report on. Additionally, for added security, CSS runs in your AWS environment so data never leaves your account.
Encryption Overview via CSS Storage Assessment
CSS’ Storage Assessment (accessible under Monitoring in the main menu), shows the totality of encryption by summing how many objects you have and how many of those objects are encrypted (figure 1).
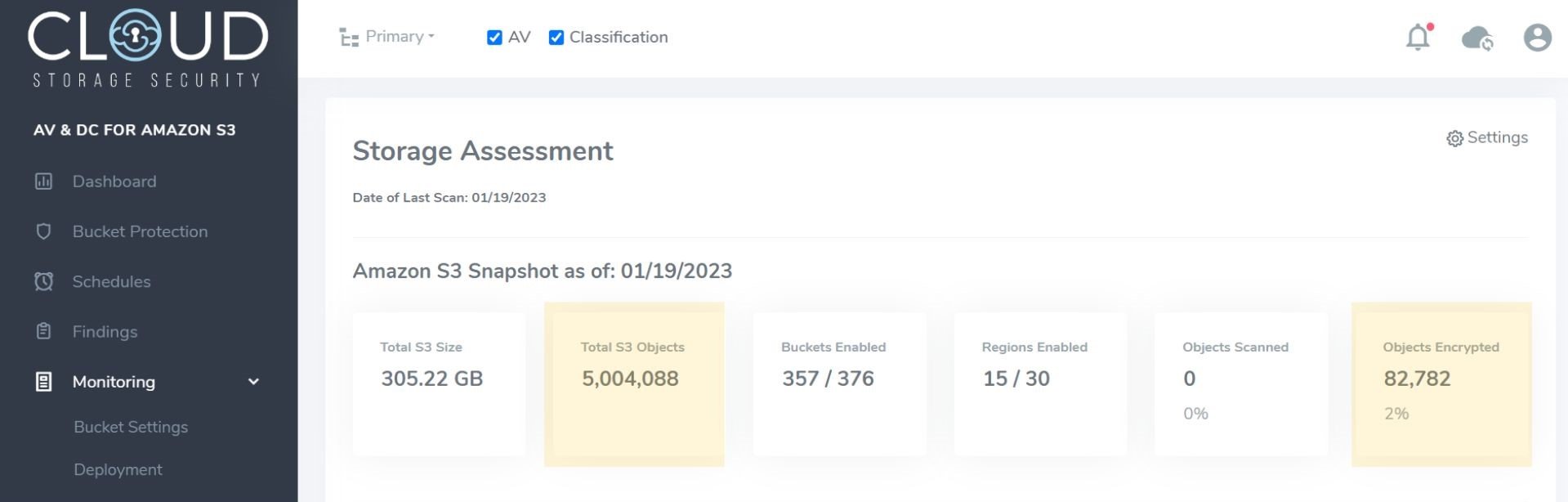
Figure 1 - Storage Assessment in CSS console showing object and encryption count
The Storage Assessment provides an overview of encryption by region – percent and bucket count (figure 2) – and also drills down into each bucket within each region to tell you the percentage of encrypted objects; it also provides a file age breakdown (figure 3).
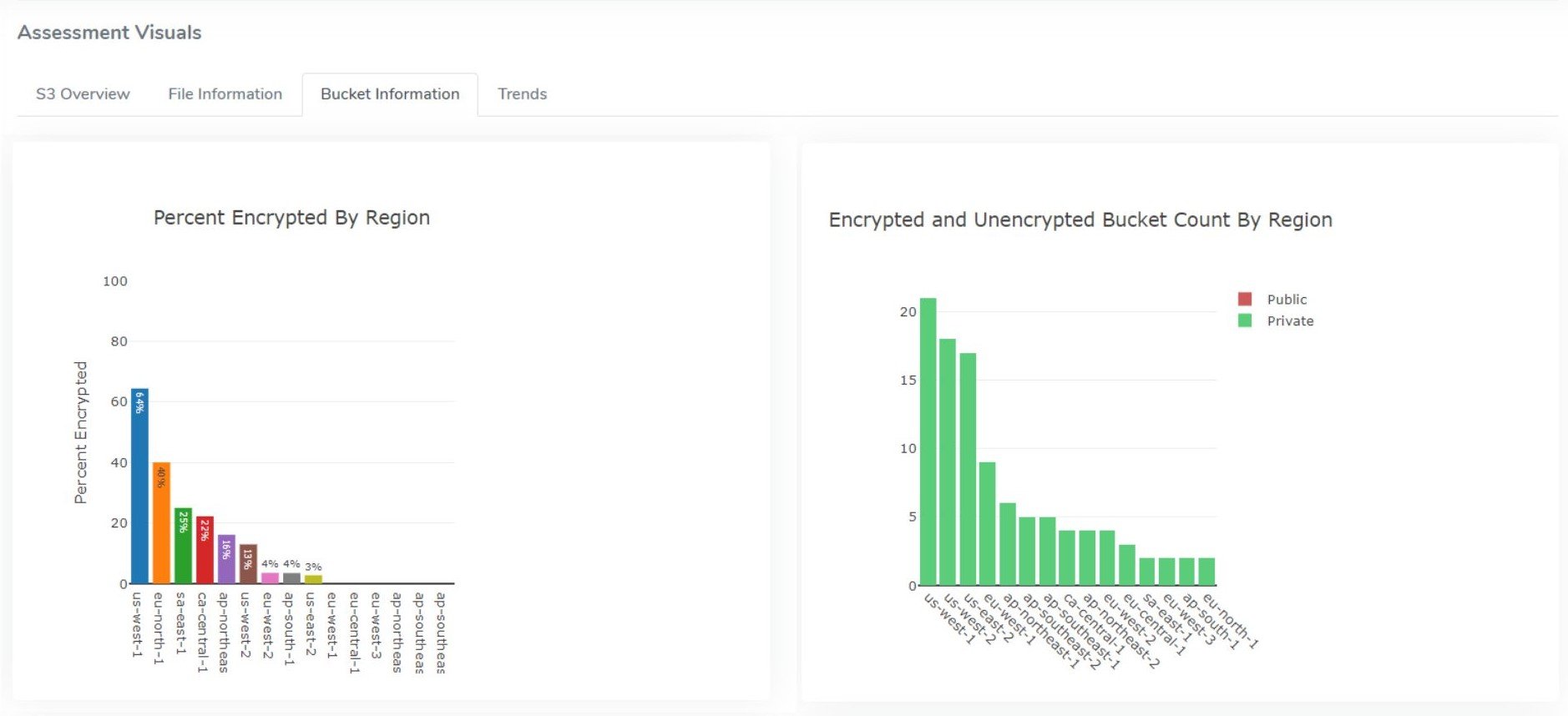
Figure 2 - Storage Assessment in CSS console showing % of buckets encrypted by region as well as the number of encrypted/unencrypted by region
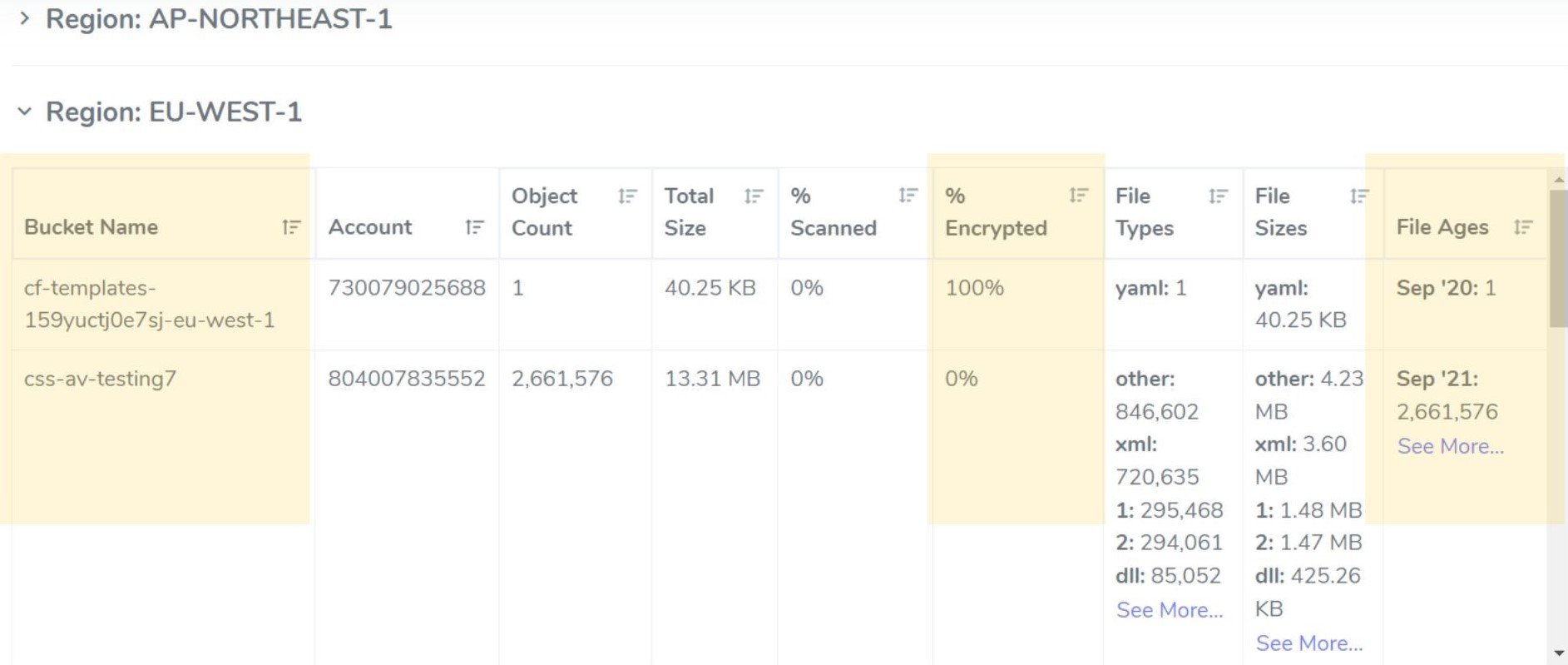
Figure 3 - Storage Assessment in CSS console showing % encrypted by bucket and age
Collectively, this information is useful because it provides you with the detail needed to investigate your encryption settings. For example, this information may lead you to investigate questions like “Should only 2% of my objects be encrypted? Is that reasonable based on the type of information we have?”, “Which buckets contain objects that aren’t encrypted that should be?” and “Which buckets contain unencrypted files older than Jan 2023 that should be investigated?”.
Encryption Overview via CSS Bucket Protection Reporting
If you’re using SSE-KMS, CSS provides additional information on encryption status via the Bucket Protection table in the CSS console (accessible via the main menu). This report provides a complete (filterable) list of your S3 buckets and their protection status that allows you to see which buckets are encrypted via a key icon next to the bucket name. Additional detail about the encryption setting is accessible by hovering your mouse pointer over the icon (figure 4).
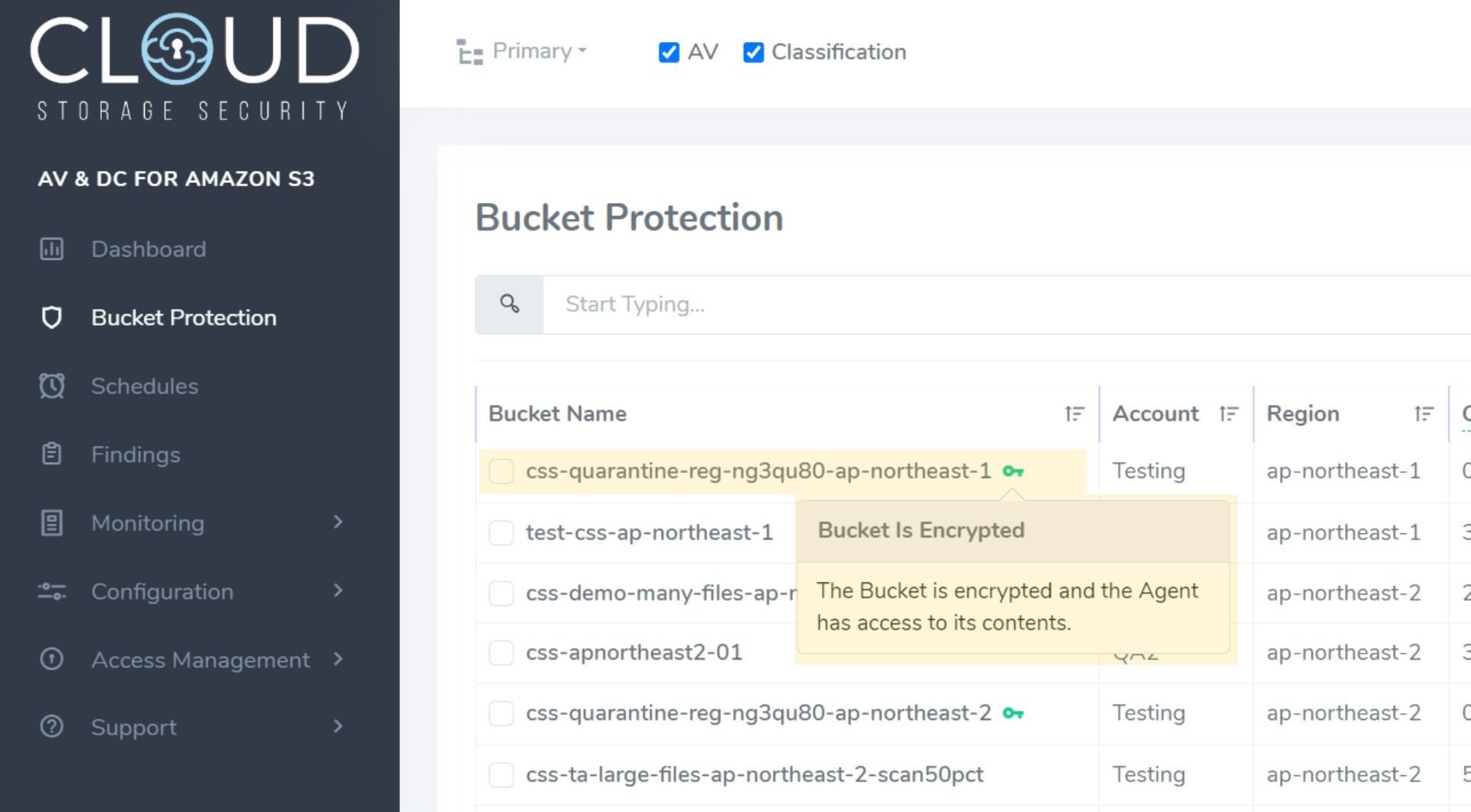
Figure 4 - Bucket Protection table in CSS console showing green encryption key and detail
You will see a green key, a red key, or no key.
A green key means KMS encryption is enabled on the bucket and CSS’ AgentRole has permission to the key in order to decrypt the bucket's contents for malware or sensitive data scanning.
A red key means KMS encryption is enabled on the bucket and CSS’ AgentRole does not have permission to the key. So, while the bucket is encrypted, you cannot scan its contents because CSS is unable to decrypt the objects. (To scan an encrypted bucket, you can give the AgentRole permissions to the key.)
No key means the bucket is unencrypted.
How to Encrypt Existing Objects in S3
Per AWS documentation, “to encrypt existing objects, you can use S3 Batch Operations to create encrypted copies of your objects. These encrypted copies will retain the existing object data and name and will be encrypted by using the encryption keys that you specify. For more details, see Encrypting objects with Amazon S3 Batch Operations in the AWS Storage Blog” or check take a look at AWS' Encryption Tutorial.
However, we’ve done the work for you.
The Bucket Settings report (accessible under Monitoring in the main menu of the CSS console), counts how many buckets are encrypted in total and with a simple “Yes” (green) or “No” (red) displays encryption status per bucket. Encrypting unencrypted buckets and existing objects is easy through the “Reconcile Encryption” option under the Actions dropdown menu above the table.
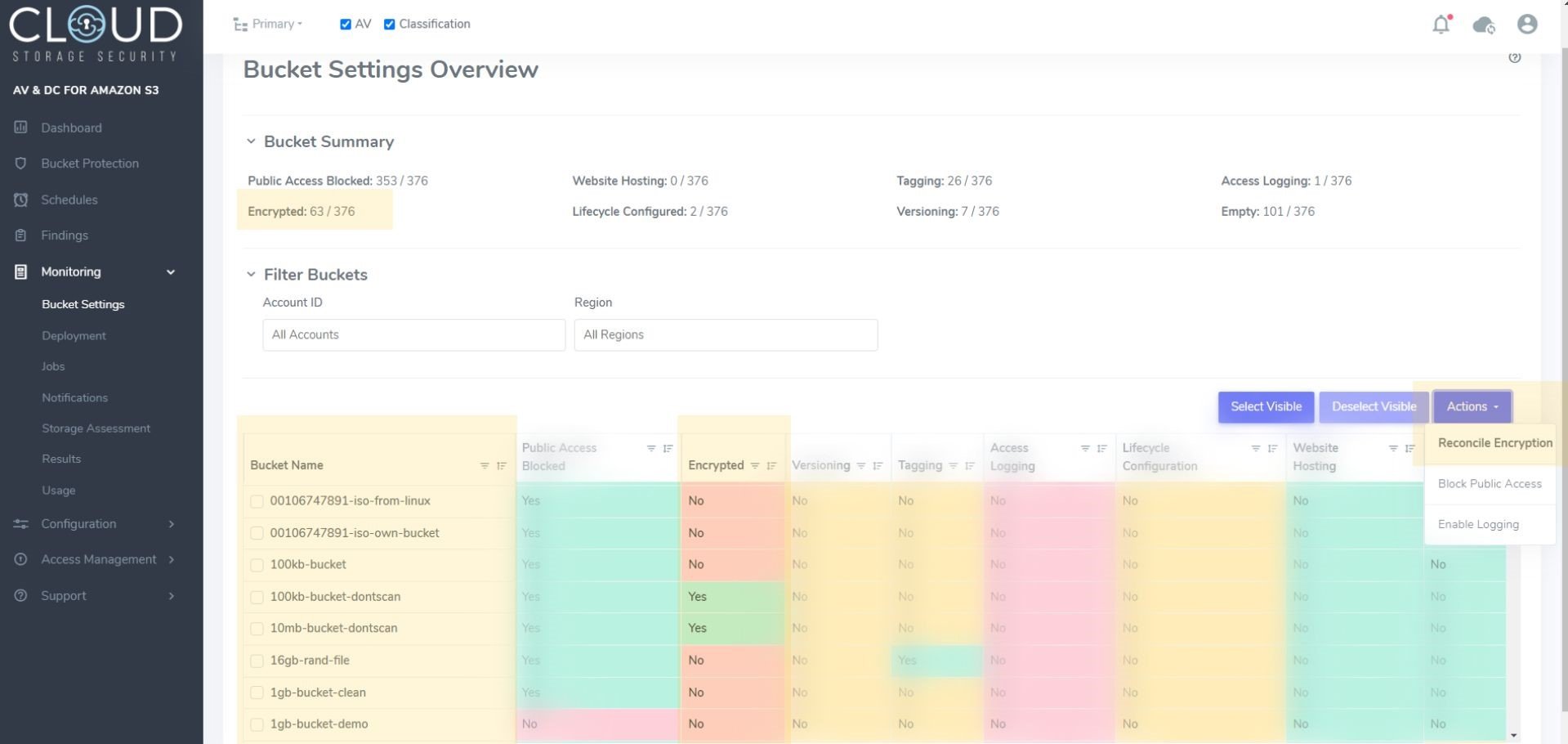
Figure 5 - Bucket Settings Overview report showing count of encrypted buckets, encryption status by bucket and the Reconcile Encryption dropdown
When “Reconcile Encryption” is selected, CSS will encrypt all objects in an unencrypted bucket with the key of your choice or default S3 encryption. For buckets that are already encrypted, any objects that are not encrypted with the same key will be updated to match the bucket encryption. To update encryption on an object, it needs to be copied over itself with new encryption configuration. A minimum of one GET call per object is required to enable encryption. If encryption needs to be updated, we will need to make an additional GET call and a COPY call.
Rather than changing the encryption status of existing objects, you may choose to be notified about what unencrypted objects you have via CSS’ Proactive Notifications. This will kick off a task that will gather all of your unencrypted files and put them into an SNS topic that is sent to the destination of your choice. From there you can selectively manage encryption.
With SSE-S3, Amazon S3 only encrypts newly created objects automatically. CSS can help you report on and manage the encryption status of your existing objects that weren’t encrypted by default as well as any new objects. If you’re new to CSS, start a free trial in AWS Marketplace and assess the encryption status of 500 GB on us. If you’re an existing customer with questions about the CSS capabilities outlined herein, contact us.


%20(1).png?width=2000&height=1125&name=CSS%20-%20Blog%20(Featured%20Images)%20(1).png)





